web port number port
This configuration option establishes the port number used by Zim applications running on a Web browser. It’s reserved for future use.
Valid Settings
A number from 1024 to 32765.
| Windows | 6005 |
| UNIX | 6005 |
web port number port
This configuration option establishes the port number used by Zim applications running on a Web browser. It’s reserved for future use.
A number from 1024 to 32765.
| Windows | 6005 |
| UNIX | 6005 |
java options <options>
The options are any valid parameters that are understood by Java when a Java instance is started. This occurs when ZimServer performs a connection to the JDBC Driver or JDBC SAM. The valid options are the ones described by the Java documentation.
java options "-Xmx64M"
backup server name <name or IP address>
The name or IP address is the location in the network where ZimBackup Server is responding to perform an online application of the data just updated by ZimServer. These files correspond to committed transactions from all databases being served by Zim Server and can be placed anywhere in the network so that they are saved in case of a disk crash.
It should be used in conjunction with Backup Port Number configuration option.
A valid Internet address.
| Windows | None is set |
| UNIX | None is set |
backup port number <port number>
The backup port number establishes the port number used by Backup Server to interact with Zim Server when applying the backup blocks to the backup databases.
Together with Backup Server Name, Zim Server establishes a connection to ZimBackup to keep sending backup blocks of data as soon as these data blocks are committed by ZimServer in its local databases.
A valid number between 1024 and 65535 not conflicting with the Server Port Number configuration option.
| Windows | 6001 |
| UNIX | 6001 |
maximum log size file-sizeThe number file-size, expressed in Kb, indicates the maximum size the log file ZIMSVLOG.ZIM can reach until ZimServer shuts itself down. This is to prevent the disk space be entirely used for logging.
A number from 1,000 to 10,000,000 (or, between 1 Mb and 10 Gb) for both Windows and Linux. The default is 1,000,000, or 1 Gb.
To optimize Zim Server performance, it’s crucial to fine-tune the configuration settings in the zimconfig.srv file. Here are detailed technical guidelines for each of the three key factors:
SHARED_MEMORY_BUFFERS: Set this to a high value to ensure ample buffer space.SHARED_MEMORY_AREAS: Increase this to allow more areas to be stored in shared memory.ini
SHARED_MEMORY_BUFFERS=1024
SHARED_MEMORY_AREAS=256
MAX_SHARED_MEMORY: Set this to a value that balances usage without exceeding system limits.SHARED_MEMORY_THRESHOLD: Define a threshold to prevent over-allocation.ini
MAX_SHARED_MEMORY=2048MB
SHARED_MEMORY_THRESHOLD=80%
IO_OPERATION_LIMIT: Set a limit on the number of I/O operations.CACHE_SIZE: Increase the cache size to reduce the frequency of I/O operations.ini
IO_OPERATION_LIMIT=1000
CACHE_SIZE=512MB
top, htop, or custom monitoring scripts can help you keep track of memory usage and I/O operations.By carefully adjusting these settings, you can achieve a well-balanced and high-performing Zim Server environment.
These options define the size of the checkpoint file, which is either the number of blocks or transactions that Zim Server will process before physically committing to disk. Both options refer to transactions that were effectively committed, meaning transactions that successfully finished.
To achieve optimal performance, it’s important to balance these options based on the size of your database and the number of users.
For small databases or a small number of users, use the following settings:
checkpoint buffers = 1000 # Small checkpoint file
checkpoint transactions = 100000 # Unlikely to reach this limit
For larger databases or higher user activity, use these settings:
checkpoint buffers = 10000 # Medium size checkpoint file
checkpoint transactions = 100000 # Unlikely to reach this limit
For even larger databases, consider increasing the checkpoint buffers value further:
checkpoint buffers = 50000 # Larger checkpoint file
checkpoint transactions = 100000 # Unlikely to reach this limit
checkpoint buffers can lead to improved performance by reducing the frequency of checkpoints, but it’s important to monitor and adjust based on actual performance metrics.By carefully adjusting the checkpoint buffers and checkpoint transactions settings, you can optimize Zim Server performance for both small and large databases. Regular monitoring and testing different configurations will help you achieve the best balance for your specific environment.
This option specifies the number of data blocks that Zim Server will keep in shared memory simultaneously. It significantly impacts Zim Server efficiency by optimizing the number of input and output operations. The larger this option, the more efficient Zim Server will be. However, it requires a substantial amount of shared memory. If insufficient real memory is available, the operating system will start swapping, which can drastically reduce performance.
This option determines how many Zim databases will be processed concurrently. The default is 3, but reducing this number to the minimum necessary will decrease the amount of shared memory required.
This option indicates the number of Zim tables (entity sets and relationships with fields) that will be processed across all databases. Keeping this number as low as possible will minimize shared memory usage.
This option sets the maximum number of users allowed to connect to Zim Server, up to the number of Zim licenses purchased. Reducing this number to the minimum needed will conserve shared memory.
These parameters define the wait and timeout durations when attempting to acquire various Zim Server internal objects. Lower values result in faster reactions to resolve issues (usually by deadlocking), allowing other users to proceed. Use the suggested values in the configuration files below.
This option specifies the maximum sizes of transactions in blocks that all users connected to Zim Server can perform simultaneously. If there are 10 users connected but only 5 performing transactions, only these will count. For example, if the average number of blocks processed is 500, the number of entries used will be 2,500. Once a transaction is finished, all entries used in that transaction are released. This number cannot be smaller than Scatter Table Links. A good approach is to calculate 3 to 5 times that number.
This option sets the maximum size for a transaction in blocks, allowing transactions to process different blocks of data up to this limit. For instance, an ADD statement creating a very large Zim file (e.g., 500 MB) will require this parameter to be at least 500,000. However, such commands are not common daily, suggesting a specific configuration for large operations. The larger this number, the more efficient Zim Server will be. A good reference is to multiply Maximum Data Blocks by two or three. This parameter cannot be smaller than Maximum Data Blocks.
blocks per read = 8
buffers per user = 1000
checkpoint buffers = 1000
checkpoint transactions = 100000
datablock timeout = 1
files per transaction = 20
first file to reclaim = 100
maximum blocks per user = 2000
maximum data blocks = 20000
maximum databases = <number>
maximum file locks = 200
maximum locks = 10000
maximum record groups = 2000
maximum tables = <number>
maximum users = <number>
object sleep = 1
object timeout = 1
pending sleep = 5
pending timeout = 5
processors = 1
quick locks = 10
reclaim object size = 1000
record group size = 256
scatter table entries = 70000
scatter table links = 50000
scatter table size = 100
secondary lock group size = 20
secondary lock groups = 7500
server port number = 6002
blocks per read = 8
buffers per user = 1000
checkpoint buffers = 10000
checkpoint transactions = 100000
datablock timeout = 1
files per transaction = 20
first file to reclaim = 100
maximum blocks per user = 2000
maximum data blocks = 50000
maximum databases = <number>
maximum file locks = 200
maximum locks = 10000
maximum record groups = 2000
maximum tables = <number>
maximum users = <number>
object sleep = 1
object timeout = 1
pending sleep = 5
pending timeout = 5
processors = 1
quick locks = 10
reclaim object size = 1000
record group size = 256
scatter table entries = 150000
scatter table links = 100000
scatter table size = 100
secondary lock group size = 20
secondary lock groups = 7500
server port number = 6002
blocks per read = 8
buffers per user = 1000
checkpoint buffers = 50000
checkpoint transactions = 100000
datablock timeout = 1
files per transaction = 20
first file to reclaim = 100
maximum blocks per user = 2000
maximum data blocks = 100000
maximum databases = <number>
maximum file locks = 200
maximum locks = 20000
maximum record groups = 4000
maximum tables = <number>
maximum users = <number>
object sleep = 1
object timeout = 1
pending sleep = 5
pending timeout = 5
processors = 1
quick locks = 10
reclaim object size = 1000
record group size = 256
scatter table entries = 800000
scatter table links = 250000
scatter table size = 100
secondary lock group size = 20
secondary lock groups = 7500
server port number = 6002
By carefully adjusting these settings, you can optimize Zim Server performance for different database sizes. Regular monitoring and testing different configurations will help you achieve the best balance for your specific environment.
The Server Log utility displays the contents of the Zim Server log file: zimsvlog.zim.

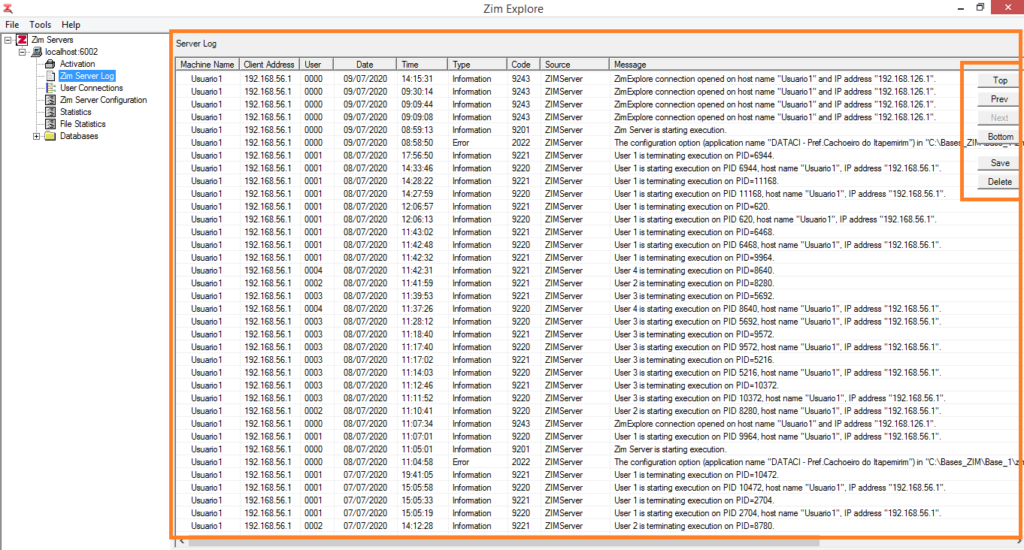
The column headers in the Server Log grid are described in the table below:
| Header | Description |
|---|---|
| Date | The date the message was added to the log |
| Time | The time the message was added to the log |
| Type | The type of message: Information, Error, Warning |
| Code | The message code. Information messages start with 9 and Error messages start with 2 |
| Source | The process that originated the message: ODBC Driver, ZIMServer |
| Log ID | Currently not used (default: 000000) |
| Message | The messaged issued by the process |
Right-click on Server Log and then click on Filter to access the server log filter

The Log File Filtering dialog will pop-up. Use it to limit the number of and the types of messages displayed in the Server Log grid.
The following drop-box options are available to limit the number of lines displayed in the log file: (Last 500 lines; Last 1000 lines; Last 1 hour; Last 24 hours; Last 7 days; and Entire Log File );
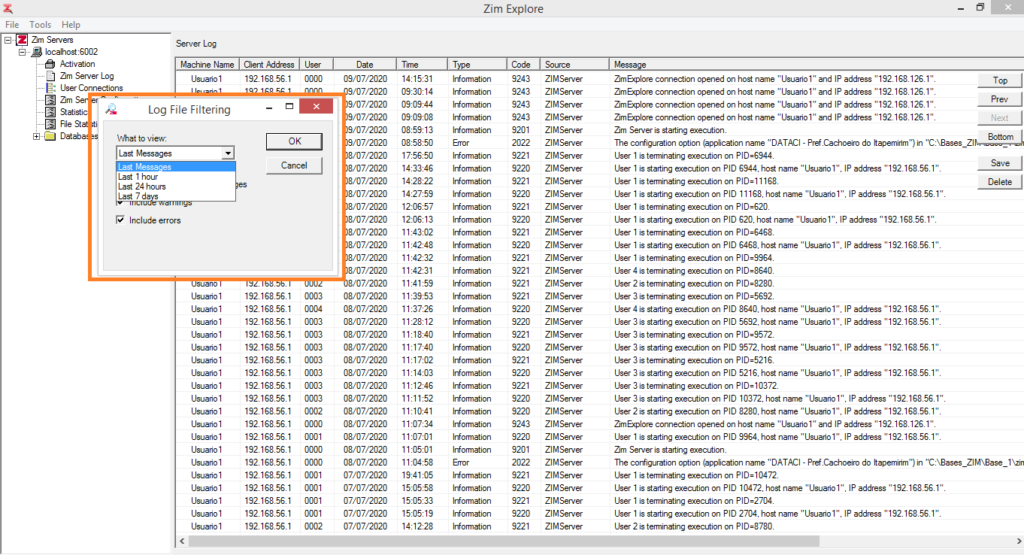
The following options, described in the table below, are used to enable or disable the displaying of specific types of messages:

| Check Box | Description |
|---|---|
| Include informational messages | When checked, messages of type Information will be displayed. |
| Include warnings | When checked, messages of type Warning will be displayed. |
| Include errors | When checked, messages of type ERROR will be displayed. |
| Automatically refresh | The utility continues to update the server log display in real time, according to the selected filter parameters. |
maximum locks locks
The number of locks is the maximum number of locks that Zim Server can handle simultaneously. This means that the sum of all locks used in all ongoing transactions cannot exceed this number. Consequently, the larger the number of users, the bigger the number of locks needed, and, correspondingly, more shared memory will be required.
The utility ZimAdmin can help to monitor the number of locks actually in use. The initial line of action would be to accept the default number and then, by monitoring the usage of these locks, increase or decrease the value according to real needs.
A number from 100 to 10,000,000.
| Windows | 1,000,000 |
| UNIX | 1,000,000 |
This option is not used by Zim Server and might be removed in future releases.
datablock timeout milliseconds
The time milliseconds indicates how long a buffer is going to stay in memory before Zim Server can use it to make additional room for new buffers being read.
When a Zim session make a request to Zim Server to read a particular block of data, depending on the configuration option Blocks Per Read, more than one block can be read and stored in memory buffers, all in the same operation because a physical read operation brings more than one block at a time.
If, sometime later, these additional buffers are required for subsequent operations, these blocks will be found in memory thus saving physical read operations. However, because they can take space from useful blocks, they are marked to expire in the next milliseconds set by this configuration option.
This very same mechanism happens when a transaction is either committed or aborted. In these cases, if a particular buffer is no longer used after the commit or the abort, then the corresponding buffer is also marked to expire as above.
The smaller the number of milliseconds, the faster a buffer can be released from memory in case of need. This is particularly interesting for very active applications or for small number of Maximum Data Blocks.
Range between 0 to 60.
| Windows | 5 |
| UNIX | 5 |
checkpoint buffers buffers
The option buffers indicates how many buffers must be written to the temporary log file before performing a checkpoint that commits ongoing transactions to disk. If this limit is reached while transactions are in process, the checkpoint will happen only after all transactions have finished to guarantee atomic transactions.
The smaller the number of buffers, less efficient will be the overall performance of the system, but the databases involved will be more often updated.
If the number of buffers is big, ZIM Backup Server, if running, will take more time to perform the backup process.
Regardless of the number of buffers, in case of a disk crash, ZIM server will automatically recover all consistent transactions present in the temporary transaction file.
A checkpoint is triggered whenever the number of checkpoint transactions or the number of checkpoint buffers happens first.
The number of buffers should always be less than the half of the number of Maximum Data Blocks; if this happens, the number of buffers is adjusted accordingly.
Range between 1 and 1000000.
| Windows | 300 |
| UNIX | 300 |